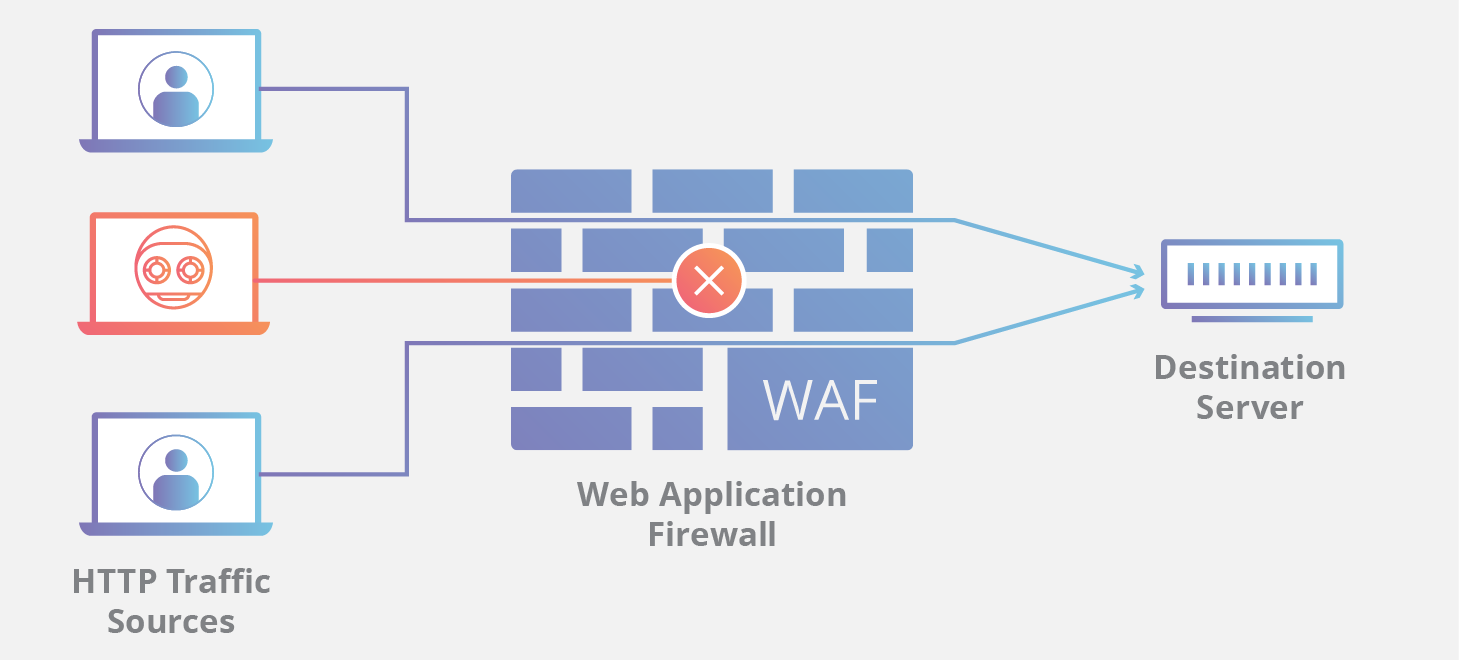
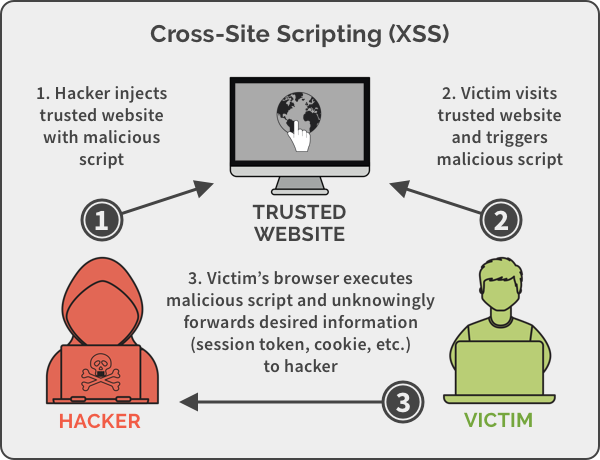
What is a web application firewall?
A web application firewall (WAF) helps protect a company’s web applications by inspecting and filtering traffic between each web application and the internet. A WAF can help defend web applications from attacks such as cross-site request forgery (CSRF), cross-site scripting (XSS), file inclusion, and SQL injection.
A WAF can be especially beneficial to a company that provides an e-commerce site, online financial services, or any other type of web-based product or service involving interactions with customers or business partners. In these cases, WAFs can be especially useful in preventing fraud and data theft. However, since a WAF is not designed to ward off all types of attacks, it works best as part of a suite of tools that support a comprehensive application security program.
Key benefits of a WAF
A WAF can provide critical protection for any online business that must securely handle private customer data. Businesses typically deploy a WAF to shield their web applications from sophisticated and targeted attacks, like cross-site scripting (XSS) and SQL injection, that might result in fraud or data theft. When successful, these types of incursions can severely compromise customer confidence and even result in regulatory penalties. The added protection that a WAF provides can help safeguard a company’s reputation and position in the market.
A WAF also lightens the administrative burden of ensuring proper web application security testing on a continual basis. By helping to proactively set guidelines and rules, application security teams are able to monitor for what should and shouldn’t be allowed through a WAF. From there, teams can receive timely notification of an attack in progress so they can respond much more rapidly to potential security incidents.
Because a WAF provides security administrators with the application visibility necessary to demonstrate compliance with regulatory standards like PCI, HIPAA, and GDPR, it can be valuable from a compliance perspective as well. Combined, all of these advantages can help a company strengthen its web application security and better safeguard customer data from evolving threats.
Stateless WAFs vs. stateful WAFs
A WAF sits between a company’s web applications and the requests coming in from the internet. Via reverse proxy, it monitors, filters, or blocks data packets as they travel to and from a web application. In doing so, it attempts to screen out potentially harmful traffic that may enable web exploits. A WAF may come in the form of a cloud-based solution, an appliance, a server plugin, or a filter.
Early WAFs, which are known as stateless WAFs, used static rules to analyze potential threats arriving via inbound requests to a company’s web application servers. Using pattern recognition, they effectively generated educated guesses on how a web application might react to a specific form of attack using predetermined models of application behavior and attack behavior. For example, stateless WAFs might check how quickly requests were coming in, whether they were originating from the same source, and other behavioral metrics that might indicate malicious activity was underway.
Stateless WAFs could perform such tasks much more rapidly than their human counterparts, but they were not adaptable or nimble enough to successfully ward off evolving attacks. A continual game of cat and mouse ensued in which attackers, upon discovering that their initial form of attack on a web application had been unsuccessful, would simply devise a new form of attack behavior that the WAF had not seen before and could not prevent. Then, when the WAF eventually received new rules that could ward off this new attack variant, the attackers would come up with yet another method for evading detection.
The second generation of WAFs, known as stateful WAFs, offers more agile defenses than its predecessor. Stateful WAFs can enrich collected data with relevant context and analyze a web application’s current threat landscape. Since they take a broader, more contextual view into account, stateful WAFs are better at detecting critical issues such as DDoS attacks and “low and slow” attacks that attempt to undermine security by flying under the radar.
WAF vs. RASP
Another technology used for monitoring and protection is Runtime Application Self-Protection (RASP). RASP blocks malicious traffic without the need for static rules using the application itself. Rather than relying on predictions about how an application might behave in a particular scenario, RASP assesses actual application behavior to detect potentially malicious activity (for example, a call to a database, a request to open a file, or a request to start a shell for the purposes of executing a command) as it occurs.
This can cut down on false positives often seen when using a WAF, giving a security team more accurate insight into potential attacks in real time. And, since it uses the application itself, RASP can still assess an application’s security even as the application is continually updated and further developed. RASP fits more easily into a continuous process because you can watch how the app behaves as you continually push code changes instead of having to manipulate the static rules for WAF. WAF and RASP can complement one another, combining forces to provide a business with comprehensive and robust application security.
Do I need a Web Application Firewall (WAF)?
With cyberattacks becoming increasingly more complex, businesses and organizations must put themselves in the best position to defend themselves and their clients from malicious intent. Companies involved in e-commerce, online financial services, and various other web-based products face a constant threat of fraud and data theft, which leaves them prone to compromised customer trust and possible regulatory disciplines.
Alongside a suite of tools, WAFs can add an essential extra layer of defense to an already-robust application security program. Security professionals can leverage a web application firewall to monitor a possible attack-in-progress by receiving alerts for activity that violates pre-determined guidelines and rules. This visibility ensures that security teams have the necessary capacity to fulfill regulatory standards, while still maintaining the utmost protection for customer data.