Imagine having to use your phone, but you can’t use any contact storage – you need to remember and dial every single person’s phone number. Sounds tedious, right? This is what a world without DNS would look like!
Although its practical use can be explained in just the above sentence, the domain name sytem has many interesting intricacies which we’ll explore in depth throughout this article. Stay tuned and keep scrolling for some interesting facts and useful knowledge about how DNS works!
Overview
Back in the 80s before DNS was introduced, computers on a network were being accessed through their IP address, which is much like a phone number.
It’s just digits.
This was useful for some time when the internet was quite small. And yes, it was small enough for this system just a couple of decades ago. With its growth though, this approach became less and less practical. We all know our closest friends’ phone numbers, but imagine what would happen if your friend circle grew to several million people in just a couple of years.
Well, this happened with the internet and remembering or writing down numbers wasn’t quite possible, practically speaking, anymore.
At one point, the scientists at MIT realized that the human brain is perfectly capable of memorizing words or phrases, and not all that potent when it comes to random number sequences. This logical, yet crucial, realization gave birth to the predecessor of DNS – the hostname service.
It was a crude solution but did serve its purpose. The hostname was just a huge file named “hosts” that every operating system has, even nowadays. It was being used during the times of the ARPANET (the biggest network before the internet came to be.)
The next logical step of this train of thought was to centralize or globalize this system. This is how the Domain Name Service (or Servers, or System) or DNS for short, came into existence. It’s a global, centralized system that gives “names” to IP addresses and makes them easier for humans to interact with and memorize.
When you type “google.com” into your browser, your browser *knows* which computer(s) that phrase is referring to. There are several steps as to how this is realized, and we’ll go through them in the next chapters.
What is DNS
DNS is the backbone of the internet. That statement is far from a precise DNS definition, but its truthfulness cannot be disputed. Without the domain name system, the entire internet wouldn’t work at all, along with all the gruesome consequences that this will cause.
The domain name service operates on several levels of abstraction, which allow for the domains to be categorized properly, in a strict hierarchical structure. These abstractions are called namespaces and are separated by the dots found in every domain. If you take for example the domain bestcloudhostingasp.net you have the following layers:
Top Level Domains
This is the “.com” portion of the domain. Unless you grew up under a rock, you would have definitely heard about “.com”, “.net.”, “.org”, and other popular top-level domains. They are the most common and also the oldest ones. There are currently more than 342.4 million domain name registrations, and “.com” and “.net” combined amount for 151.7 million of them.
Some top-level domains are globally usable like the aforementioned, but there are also those that are restricted to specific organizations or countries. The “.edu” gTLD is reserved for educational facilities, the “.gov” for government organizations, and so forth.
Fun fact about gTLDs: The extremely popular .TV gTLD which is being widely used as a reference to “television”, is actually the country-code TLD (ccTLD) for the country Tuvalu, which generates a considerable amount of its national net worth purely because of this coincidence!
Country-code Top Level Domains
Country-code TLDs are top-level domains used to describe sites that operate in (or from) specific countries and regions. They are useful for branding, local businesses, and for international sites with numerous local iterations.
The online giant Amazon has a dot-com version, dot-de for Germany, dot-uk for the United Kingdom, and so forth. This approach boosts local market penetration, bypasses language barriers, and makes calculating shipping costs (and customs taxes) much easier.
Mind, ccTLDs are still TLDs and not secondary domains.
Second-Level Domains
Second-level domains come before the dot in dot-com or dot-us. In our example, this is the “
New gTLDs are created through a lengthy, expensive application process and evaluation done by ICANN (the regulatory body for all domain names, among other things), and you, as a user, can only use the existent set.
Ultimately, ICANN regulates all domain names in existence.
On the other hand, second level domains can be whatever you want it to be. As long as the name is free you can register it. However, considering the size of the internet, this is not always an easy task.
Fun fact about second-level domains: The shorter and more recognizable the domain is, the more valuable it is. There are a huge number of companies and people who profit from registering domains which might generate commercial interest and then selling them for a huge gain. A new domain name registration usually costs between $1 and $100, but buying a “premium” domain from someone who obtained it for the sole purpose of reselling it can often come in the tens or hundreds of thousands of dollars!
Subdomains
Subdomains are governed by the owner of the second-level domain, and they can create any number of subdomains in the DNS zone. For this reason, you will quite often see utility subdomains like “shop.mydomain.com” or “blog.mydomain.com”.
Creating subdomains is free and they are very useful for providing additional information in the URL bar. In companies, you would see them nested even more frequently, where location, type, purpose, etc., are being referenced in there too. For example “servers.storage.eu-west.region1.google.com” could easily be a legitimate domain name for a Google server.
How DNS works
There and back again – the lifecycle of a DNS request
When you submit your request for the domain bestcloudhostingasp.net your browser first checks the local operating system for any entries of it.
Remember the “hosts” file we mentioned earlier? It’s still around and it’s the first thing place where the OS looks for IP addresses bound to that domain.
If it doesn’t find a reference in there, then the OS checks with your internet service provider.
This is the beginning of a process called DNS record lookup, as the ISP sends the request to the global network to locate the resource (website, typically) the end user wants. Due to the amount of DNS lookups being performed for each provider (literally, millions per second), ISPs usually keep a cached version of the entries so they don’t have to make the lookups every single time the same resource is requested.
This step of the process is handled by the recursive resolver. A noteworthy fact about the resolver is that it groups the requests it receives in batches. Essentially, this creates a cache database so that a small number of requests can serve a considerable amount of users. This saves network traffic, which is extremely important when we keep in mind the scale of the internet.
If your internet service provider doesn’t have the IP you OS wants then your request is propagated further up the chain by the ISP (which will then add the return to its DNS cache database.)
Root Nameservers
If your request doesn’t find an answer anywhere in the cached data along the route, it gets to the root nameservers. They are the authority which contains every single DNS record and are responsible for controlling the authenticity and availability of all of them. The root servers redirect the traffic for each gTLD to the respective authority.
Once your query gets to the root nameservers, they check for the respective gTLD authority. They scan the domain name from the right-hand-side first. (Technically, domain names are read from right to left.) For example, for any “.com” domain name, they redirect the query to the “.com” TLD name servers – those of VeriSign.
The TLD name servers already know which gTLD they are responsible for, so they check the second level domain. In the case of our bestcloudhostingasp.net query, the TLD name servers will check for “bestcloudhostingasp” and through their optimized algorithms will return the result.
TTL
During the return of the request, our intermittent servers (the recursive servers) will store the obtained DNS values for a specific period of time. This is called the “time-to-live” (TTL) that any domain record has. The TTL duration is set with the record itself.
If you want to have your record refreshed often by the DNS chain of servers, you can set a short time-to-live. This is quite often unnecessary, since DNS records don’t change frequently for a working domain.
After all this, the request makes it back to your computer, where you save the record in your browser as a local reference, and the browser itself sends a request to the IP that you received for that domain.
What a ride, eh!
Considering that data exchange on the internet is close to the speed of light over fiber cable, this whole series of technically complex events only takes milliseconds.
Fun fact about the root nameservers: There are only 13 root nameservers! In reality, each of them is comprised of a cluster of machines to provide the necessary computational power, security, redundancy, and bandwidth. If even one root server happens to be down, the impact on the internet is huge. Countless websites will stop resolving; even huge ones that are always available will be down. The 13 servers are operated by:
VeriSign, Inc., University of Southern California (ISI), Cogent Communications, University of Maryland, ASA (Ames Research Center), Internet Systems Consortium, Inc., US Department of Defense (NIC), US Army (Research Lab), Netnod, VeriSign, Inc., RIPE NCC, ICANN, and WIDE Project
DNS Zone Dissection – Types of Records
A term you might encounter while setting up your website, especially if the domain name is registered at one place and the hosting is provided at another, is A record or DNS records. All website-related DNS records are part of the site’s DNS zone.
In turn, the DNS zone serves an administrative and technical function. Strictly speaking, the DNS zone definition states that this is a segment of the entire domain name system that is under the managerial authority of a single administrator, be that a legal or private entity.
I know, it sounds like a technical nonsense.
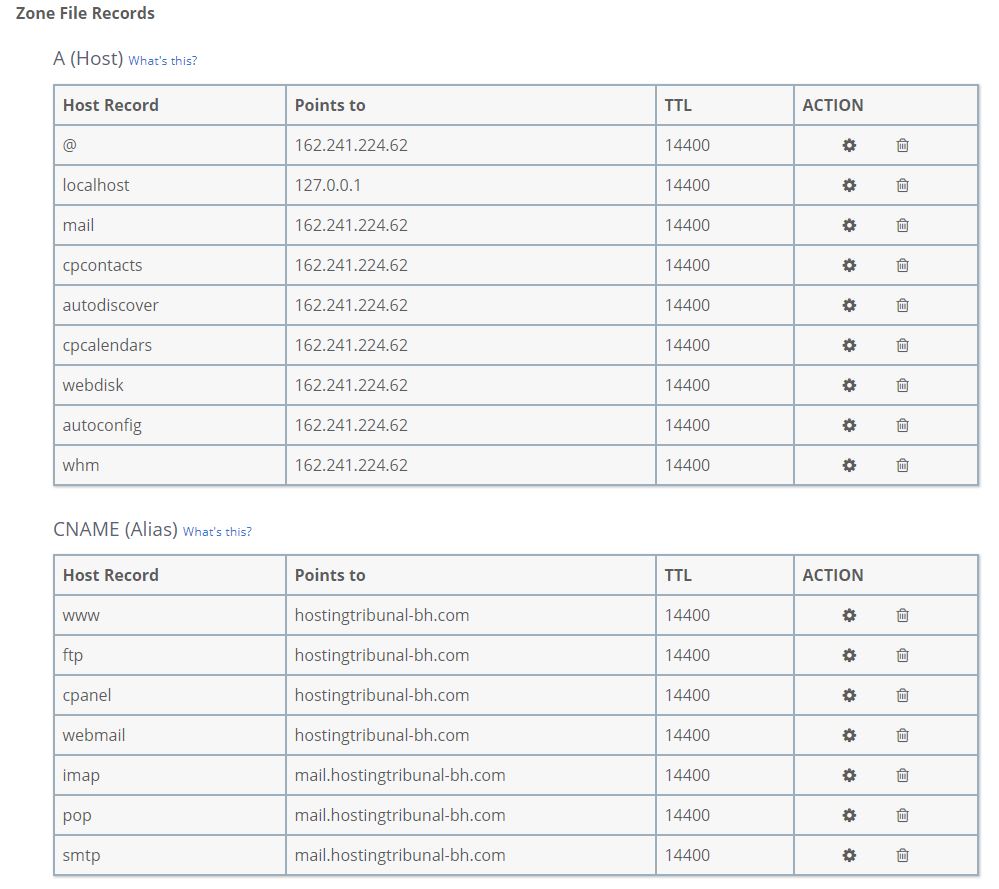
A detailed DNS zone with numerous entries. Tread carefully.
All the same, I’ll leave it at that and will focus on the practical DNS zone aspects that concern website hosting directly.
In web hosting, several interconnected services need to be directed to the proper servers for a hosting service – website, database, email – to work, and that coordination is regulated by the data stored in the DNS zone. The zone is a collection of DNS records sorted by their individual types; the content is called a DNS zone.
For example, the record that tells a domain name from where (from which server, that is) to load content (also known as “the website) is stored in the main A record. Quite often the www record also gets an A record.
However, there are other types of records for the mail services, for the additional services, ownership authentication, and others.
Main Types of DNS Records
A Record
The A record is a DNS record that relates a domain name to an IP address. This is how your website’s home server can be found on the internet. It is the A record that associates the website (the content) with its designated domain name (address).
AAAA records
The AAAA records are exactly the same as the A records, but instead of using IPv4 addresses, they use IPv6, which is already a necessity. When the internet was created, the amount of 4 billion addresses provided by IP version 4 seemed orders of magnitude greater than what would ever be needed. However, with the exponential growth of the internet and the explosion of devices connected to it, this is no longer the case. IPv6 was introduced to battle the exhaustion of the IPv4 pool without changing much how DNS works as a whole.
CNAME Record
The CNAME record is quite similar to the A record, but it binds a domain name to another domain name. This way you can hook subdomains of your domain to external domains without worrying about changing their IP addresses – you will be referencing directly to the other domain name instead.
MX Record
The MX record is the one that directs where the mail server, and quite often “servers” are located. In order for your website to open, there needs to be a web server which serves the website data; however, the emails are sent and received by a mail server, hence the purpose of existence of the MX record.
MX records have a specific property called priority. The MX server priority is designated with digits, starting with zero. This is done for redundancy reasons, mostly, so that several mail servers can be associated with a single domain name. If the server with priority 0 doesn’t reply to the request, the one with the next number is being queried and so on.
SPF Records
SPF records is a TXT record (text-based record) used for determining the authenticity of the mail services. As the mail protocol is quite old and hasn’t seen many (if any) updates over the last decades, additional security measures are introduced every now and again. Most of them help determine whether the sender of the email is the person he claims to be. SPF records are one of those mechanisms.
PTR records
PTR records are reverse DNS records which are the exact opposite of A records. They bind IPs to domains. This way when you query an IP, you can get meaningful information as to what domain name it’s associated with.
NS Records
The nameserver records are one of the most important ones as they tell the domain name which DNS zone to use. Generally, you can create a DNS zone in any DNS server and have different records for it. For example, you can create a valid DNS zone for “google.com” and send it to your website. Does this mean that all the traffic for Google is now yours? Well, no, because the authentic Google.com NS (nameserver) records are saying which exact nameservers are containing the correct DNS zone. Quite handy.
What is DNS Caching
Throughout this article, we’ve been talking about huge (and I mean HUGE) numbers which give us a real impression of the scale of the internet.
In that sense, it’s extremely important to manage resources properly. In many systems, one unoptimized request is alright, having 1000 is occasionally manageable, and having millions upon millions every single second…
Well, this when every single link in the chain needs to be perfectly optimized for it to serve its purpose.
This is where DNS caching comes in.
Instead of every single request reaching the TLD root nameservers, the vast majority of them are served intermittently by cached results. There’s no need for the request to travel all around the world if your internet service provider already has the answer.
There are several layers of DNS caching, the first one of which is right in your browser. Every single major browser has DNS caching built-in.
This means that when you visit a website often, your DNS query doesn’t even leave your computer.
The browser knows the IP of that car dealership website you’ve been visiting secretly from your wife and simply requests the site content directly, instead of performing a full lookup throughout the domain name system for it.
If your browser doesn’t have a particular record cached, it will check with the operating system. Even if you don’t frequent the internet much, you will still be amazed at the amount of DNS cache your OS has.
Windows users can open the command prompt and type the following command: “ipconfig /displaydns”. This will give you a huge list of locally cached DNS, like so:
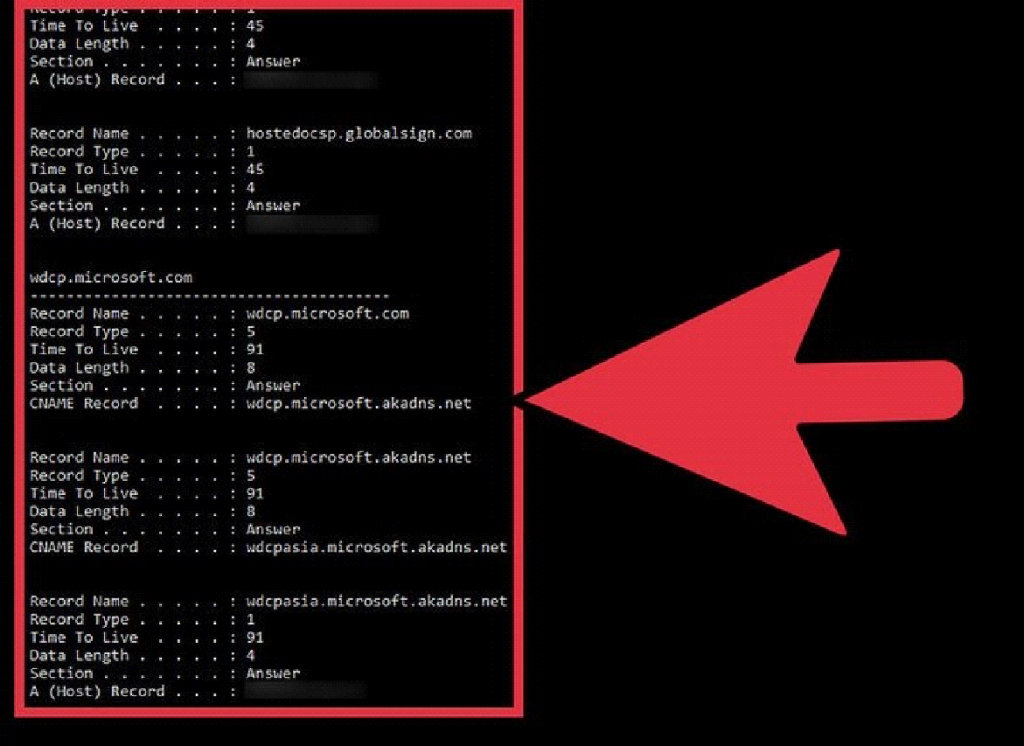
The DNS records of a regular Windows OS.
All of the servers through the request pathway are caching results for a time equal to the TTL we mentioned earlier. This multilayered caching reduces the total amount of requests that go all the way through the DNS hierarchical chain.
DNS cache can also be manually purged in a process called flushing. Server administrators can do this manually, or it can be scheduled for automatic execution. Put simply, this is the process of removing all cached entries in the system and awaiting fresh ones.
Security Concerns
As is with every system on the internet – there are always security issues and considerations involved, and DNS is no exception.
A particularly common exploit is DNS cache poisoning. This happens when an authoritative server is maliciously set to provide wrong results for a DNS query.
A simple example of DNS poisoning would be that “google.com” always points to the Google servers and opens the infamous website. If a particular server or set of servers provide wrong records to the upstream DNS searchers, then google.com can resolve to any IP that the hackers have set. This is usually accomplished through viruses or glitches in the DNS protocol.
Another exploit is DNS amplification attacks, where the DNS servers are being spoofed by the wrong DNS query requester address and they all return data to the same IP. This way thousands of servers can send a DNS response query to a particular machine until its available resources are depleted. In this type of malicious exploit, the attack isn’t toward the DNS servers themselves; instead, they are used to bring down other servers.
DNS tunneling is another attack on DNS servers. Basically, it is a way of transferring malicious data from one machine to another. The data itself is encoded in the request sent to the server. Upon responding, the server creates a two-way connection for data transfer and this often times enables unauthorized remote access to the server itself.
A type of local DNS exploit is DNS hijacking. This involves editing the networking information on a particular machine so that it will resolve its DNS queries toward a malicious DNS server. Generally, your system would use trusted DNS servers to obtain records upstream, but if that data has been altered, you can end up with any DNS records that the attacker has set onto the malicious DNS server.
A DDoS (Distributed Denial of Service) attack is a NXDOMAIN attack which uses a huge number of servers to make requests toward a non-existent domain, flooding the DNS servers with requests in the process. Every machine has limited resources, and can perform a limited number of queries before it starts adding delay or services start crashing. Once the server is overwhelmed with requests from the attackers, it cannot serve any legitimate user requests anymore.
Conclusion
Today we looked over what is DNS, the principles of how it works, and the intricacies that can lead to misuse and abuse.
The topic is quite broad and filled with technical specifications, but this information should be more than enough for you to have an educated conversation regarding DNS with your friends and colleagues.
As a cornerstone of the internet as a whole, the domain name service is a topic that every professional and hobbyist should understand at least a bit. Hopefully, you now have that necessary understanding and can venture deeper into the DNS specifications if this article has sparked your interest.
FAQ
What is an example of a DNS?
The Domain Name Service (DNS) is a worldwide specification that allows for human-readable names to be associated with internet IPs. You, as an internet user, use DNS on a daily basis through every single website you visit, when you check your email, and when you make an internet call. Each of those operations performs a DNS query, so that your computer can learn which server the request should be sent to.
Why would you use DNS?
DNS is used to resolve any service on the internet. You can always point your services toward an IP, but IP addresses (especially IPv6) are much harder to remember, and also the IP behind a service can change. DNS handles those changes for you. For example, the servers hosting “google.com” can change, but you don’t need to check or memorise them – the DNS handles those changes so you can always type “google.com” and reach the familiar website regardless of any changes the actual IP behind it can undergo.
What is the DNS IP address?
The IP address is a protocol created so that each machine on a network can be assigned a unique identifier. Generally, every single IP is unique to a machine and allows the said device to be reached over a network, or, in the most common case, over the internet, which is the biggest network in the world . When you perform a DNS query, your request reaches an IP that is the address of the machine you should direct your request to.
What is DNSSec?
DNSSec is a specification which allows for DNS to be hardened for greater security. It’s a set of extensions of the DNS protocol, which allows it to verify the origin of a request and the integrity of the data being submitted and requested, by providing a signing mechanism to the requests. DNSSec stops manipulated data from being submitted to the servers in order to alter the records maliciously.
What is 1.1.1.1 DNS?
The 1.1.1.1 DNS is a rather new (launched on April 1, 2018) DNS recursive name server, which has been created by CloudFlare in partnership with APNIC. CloudFlare are a leading international company in the DNS and anti-DDoS fields. The purpose of the name server is to provide the fastest DNS resolves and focuses on privacy. Besides CloudFlare’s 1.1.1.1, other famous DNS servers are Google’s 8.8.8.8 and 8.8.4.4, which many system use.
What is DNS lookup?
A DNS lookup is the process of sending a query for a specific domain or IP and getting the record that corresponds to it. DNS queries happen every single time you access a website or a web-related service, since there always must be a server (with its designated IP address) that serves that request.
What is DNS server?
The DNS servers are machines that are used to host an application that saves, caches, and serves DNS records. The most popular application for the purposes is BIND, which is also the one that some of the root nameservers are using. Once a server has the application properly set up as a nameserver for a particular domain, it becomes a DNS server. Other types of DNS servers are the recursive DNS servers which are being used solely to maintain and provide DNS records.
What is DNS zone?
The DNS zone is a collection of DNS records which provide meaningful information for a particular domain. This includes records for all services related to the domain – the web server, the email services, the authentication records, the text records and many, many more. DNS lookup requests can be performed toward a specific record in the DNS zone, or for the DNS zone as a whole.
What is DNS?
The Domain Name System is a worldwide specification on the internet that allows for “names” (or domain names) to be mapped to IP addresses. It has been created since it’s rather hard for humans to memorize number sequences like IP addresses, and it’s far easier to memorize words since you can associate meaning with them. For example remembering the IP “157.240.1.35” and typing it every single time you want to check your social media account might be tedious, however “facebook.com”, which points to that IP, is far more convenient.